
18 Nov Protecting your Digital Identity
In a nutshell
-
- We are relying more and more on our online accounts for every aspect of our lives
- Most people have very weak security on these accounts, leaving them vulnerable to hacking
- Use Password Managers to track and manage unique complex passwords for each site
- Use Multi-Factor Authentication to protect the most sensitive accounts
Protecting your digital identity by garethbarr.com
As we conduct more of our lives online, the use of unique complex passwords, password managers and multi-factor authentication (MFA) becomes increasingly important to our security. Please remember to subscribe to this channel.
Cybercrime and identity theft continue to be a critical everyday threat, so this article will explore how important it is to have strong security on your online accounts, and how easy it can be to take steps to protect yourself. We will be focusing on security for individuals and families, rather than business, as these concepts are broadly understood in the corporate world.
If you’re anything like me, you probably started out using the same password for any accounts you created online, so you wouldn’t have to remember lots of passwords. That might have been OK back in the early days of the internet, when all you were trying to protect was your email account or maybe a personal website, but as our lives have become increasingly digital, we now need to protect things like our money, our health information, and even our ability to vote – things so important and sensitive that we can’t just use our old methods to protect them.

We truly live in a digital age. It’s easy to use technology to do things like book a holiday, fill a prescription, pay a bill, order some clothes, or find your “perfect” date. We sometimes forget the relative complexity of the pre-digital age where, to plan a trip, we would visit a AAA store and a real person would use a highlighter to draw our route on a physical map. Today, we simply hop into the car, enter the destination on the sat-nav or an app on our phone, and let the car guide us to wherever we need to be, even telling us when and where to get gas.
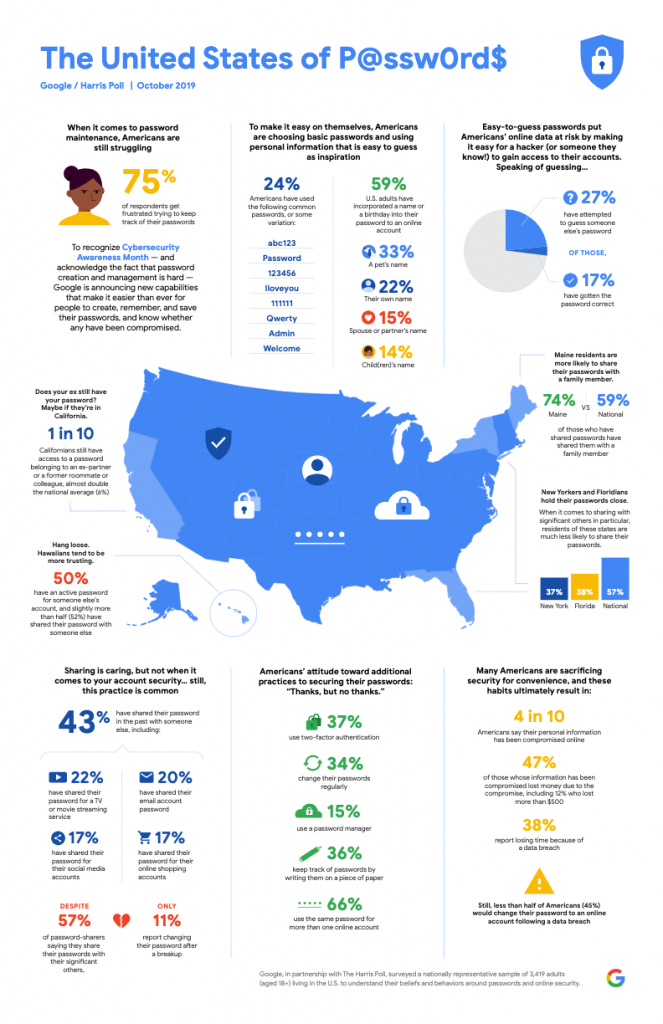
We often take this convenience and flexibility for granted but, unfortunately, as the value and sensitivity of our Digital Footprint has increased over the years, the way we protect it has simply not kept pace. A US survey by Google, taken in 2019 in partnership with The Harris Poll, showed that around two thirds of people use the same password for more than one online account. Even worse, nearly a quarter of people have used simple passwords like Password, Welcome, Admin & 123456, and nearly 60% of adults included the name of a pet, spouse, child, themselves, or birthday as part of their password!
Is using the same password really such a bad idea?

Well, if we use the same password across all our accounts, then whenever any single one is compromised, they all are! Let’s say, for example, we use the same username and password (collectively known as credentials) for our grocery store account as we do for our bank account. If the grocery store systems were to get hacked, then the hackers who managed to compromise that grocery store could potentially use our compromised credentials to gain access to our bank account, too!

You may be thinking that it’s unlikely that those hackers would know which bank we used, so wouldn’t know where to use our credentials, but in fact they don’t necessarily need to know where to use our credentials – there is a whole industry built around exploiting this information.
Many hackers steal personal information and credentials and resell them on the dark web, which is a part of the internet not visible to search engines and often used for dubious or criminal activities. It is quite common for hackers to buy and sell batches of compromised credentials this way, and there are even toolkits for sale that allow them to use these credentials in an automated way across many different sites. To speed up this process, they can even rent computing time from large botnets, which are networks of compromised computers out in the wild, under the control of other hackers!
If we use a different password for each site, then the only thing that is compromised when those credentials are stolen is that site. In other words, using unique site passwords limits the potential fallout of a password being stolen – it limits the blast radius of a security compromise.
Clearly it makes sense that we should not reuse credentials across different websites or applications, but that means that we have to keep track of different credentials for each site – as many as 70-90, according to that Google study. This is incredibly challenging to keep track of!

How do I remember all these passwords?
Trying to remember a myriad of passwords, especially ones that are rarely used, is a huge challenge. Many of us deal with this by keeping them simple and writing them down somewhere “safe”, for fear of forgetting them. Unfortunately, this leaves them vulnerable to physical theft instead, where burglars could potentially get our credentials as well as our home contents when they break in. A better solution for keeping track of these credentials is to use a password manager.
What is a password manager? Simply put, a password manager is software that allows us to store our credentials for all the applications and websites we use, safely and securely. The best password managers offer a range of features, like password generators, family sharing and site breach alerts.
This sounds like a fairly simple solution, right? Well, that same study by Google and The Harris Poll I mentioned earlier shows that only around 15% of people use a password manager to manage their passwords. My theory here is that many less technical users are simply unaware of these kinds of tools, but it could also be a resistance or lack of trust of the password manager providers. After all, it would seem that we would be handing all of our passwords over to a third party and trusting them with our most sensitive data.

How safe are password managers?
All serious password manager tools use strong encryption to protect our credentials, and can only be unlocked by a secret known only by us, which means that even the service provider cannot access our passwords. This is inherently more secure than keeping track of our credentials by writing them on a piece of paper – something that that same Google study showed over one third of people do!

It’s worth noting that brute-force attacks, where every possible combination is tried, could technically break through pretty much any encryption, given enough time and computing power. However, if we use something like 1Password, which uses AES-256-bit encryption, it would take many trillions of years to try every possible encryption key combination to break into our vault, even using a supercomputer, or the combined processing power of 2 billion high-end PCs – which makes it effectively impossible to crack with current technology. To be overly technical, it is possible that emerging technologies like quantum computing will change that situation, but these are not generally available right now, so therefore are largely irrelevant.
You can find out more about the strength of AES256 encryption here, and 1Password provide some excellent information about the security of their product here.
So, what password manager should I use?
There are a number of good password managers, including:
1Password is my personal favorite, Keeper is fairly robust, and LastPass is free, but a little basic in my opinion. If you want a good independent review of some of the more popular password managers, PC Magazine has a 2020 review here.
There are also basic password managers built into things like Google Chrome, Apple Devices (Keychain), and Microsoft Credential Manager, but these tend to be limited to specific ecosystems, and extremely limited in their capabilities.
Personally, I like 1Password, because
- It has great browser plug-ins, which make it easy to save and enter usernames and passwords on all devices
- It holds different types of information, like login details, credit cards, drivers’ licenses, social security numbers, passport information, and even freeform text.
- There is a family option, where each person has their own private vault and the option of also using shared vaults
- It lets me know where I have used the same password
- It lets me know which passwords have been exposed in hacked password databases
Is that all I need to do?
Unfortunately, although using a password manager is a great start, it isn’t going to be enough to really protect our identity. There are several other things that we must do to really have a strong digital identity:

ALWAYS use strong passwords
This is really important. As mentioned earlier, people typically use passwords that are easily guessable or hackable, such as names of pets, friends, relatives, a hobby, etc., sometimes tacking on a number as well. The problem is that real words are very easy to crack using brute-force techniques.
A strong password is one that has a minimum length of something like 12 characters, and a combination of upper- and lower-case letters, numbers, and special characters. This is important because the longer we make our passwords, and the more types of character we use in our password, the more complicated it is for a hacker to work through all the possible combinations.
As an example, a simple 5-character password that uses only the letters a through z has nearly 12 million possible combinations. If you use upper-case, lower-case, numbers, and special characters for that same 5-character password, the number of possible combinations increases to over 2 billion! Likewise, if you double the password length to 10 characters, there are over 141 trillion potential combinations!

Replace existing passwords
We need to go through all our current passwords, even if they are not weak, and replace them each with unique strong passwords, ideally ones that have been generated by a password manager. This can take a while, so we should start with the most valuable and sensitive ones. This will ensure that we have no weak spots in our existing accounts, and are not using shared passwords. It has the added benefit that if any of our existing passwords have already been compromised, they will no longer be of use to a hacker.
Use common identity providers like Google, Facebook and Apple wherever possible
You’ve probably noticed that many sites now ask if you’d like to sign in with a well-known identity provider like Google, Facebook, LinkedIn, or Apple. (There are many other reputable providers out there, too.)
This can be a particularly good idea, because it means that instead of creating credentials for each site we use, we’re actually relying on identity providers to validate that we are who we say we are, then pass that on to the site we are trying to log in to. Effectively, these identity providers are representing to other websites that they have confirmed our identity; our password is never sent to, or stored at, those other websites.
You may be wondering whether this contradicts my earlier statements about not using the same password on multiple sites, since we would effectively be using the same password to access multiple sites. The difference though is that in this situation, if one site using our ID were to get compromised, hackers could not get our password, and therefore couldn’t access any other sites using our credentials; they would only be able to access our data in the compromised site. This is quite different from a situation where we are using the same password in multiple accounts, where anyone getting access to that one password would have access to all sites using that same password.
A challenge with this approach is that our Facebook or Google credentials are now effectively like a master key to other sites, meaning that if someone were able to get THAT password, they could login through Facebook or Google to access our other sites. But, if our Facebook or Google account WERE to be compromised, we would only have to change that one password to protect all of those sites. This is both easier and safer than having to go through each of our accounts that used those same credentials, changing them individually.
If this is such a good idea, why don’t we use this approach for everything? Well, one problem is that it isn’t available everywhere. Some sites only take one of these providers, some take all, and some don’t take any. This means we are still likely to need to keep track of multiple usernames and passwords. Also, many people are concerned about how their login data might be used by these identity providers, or simply don’t trust companies like Google and Facebook to protect their data.
To provide additional security, the major identity providers in this space have an extensive set of sophisticated security measures in place to try to detect unusual behavior and let you know if it sees something suspicious. However, because these particular accounts provide access to multiple sites, there are still more things that we need to do to protect them properly…

Use Multi-Factor Authentication (MFA) for your most valuable accounts
Multi-Factor Authentication is basically a more secure way of proving that we are who we say we are, by requiring us to provide more than one type (or factor) of proof. The types of proof that can be used typically fall into the following three buckets:
- Something you know
This is usually something like a password or PIN. - Something you have
Common examples include a phone number, a hardware or software-based security token, a USB device, or a Near-Field Communications (NFC) device. - Something you are
These are generally biometric identifiers such as fingerprints, facial structure, or iris pattern.
Requiring the use of two of these proofs of identity (known as two factor authentication, or 2FA for short) significantly reduces the risk of someone impersonating us. Consider, for example, if we lost our physical security token. Someone else might find it, but they wouldn’t be able to use it without also knowing our password or having our fingerprint or other biometric.

Most people have been using two factor authentication for much of their lives without realizing it. For example, each time we use an ATM, we are presenting something that we have: the card itself, and something that we know: our PIN.
This is especially important for any sensitive accounts, including:
- Bank accounts
- Government IDs (driver license, passport, etc.)
- Social Media accounts
- Accounts that can be used to access more than one account
There are several approaches we can use to achieve this objective, but in my opinion, software-based tokens have the best balance of security and ease of use compared to physical devices or phone/SMS-based validation, particularly because biometrics are not broadly accepted yet. There are several free tools we can use to store software tokens, including Microsoft Authenticator and Google Authenticator, which are both apps that can be installed on a smartphone. Some password managers also offer the ability to store software tokens along with our credentials.

Use a password manager to store your MFA tokens
Because we are using MFA for a number of more sensitive accounts, we now need to manage a number of software tokens – one for each account – in addition to our credentials. This is one place where some of the better password managers really help, by managing the soft token for each of these accounts. By having credentials and tokens stored in the same place, we can have a simplified logon experience with only one place to go to get these details.
As an example, 1Password manages tokens in the same way that the Microsoft and Google Authenticators do, but has the additional benefit of keeping it in the same record as the username and password, and even helps with entering the code if we use the browser plugins. This means that we can potentially have access to our tokens and credentials on our mobile devices and our computers, or even our home and work computers at the same time. This is a much more convenient than using something like Microsoft’s or Google’s Authenticator programs which are tied to a specific device – which can be inconvenient if that device is lost!

Protect your password manager account with separate MFA
Because our credentials and soft tokens are now in one place, it is critical to protect THEM securely using MFA. Without this, we effectively bypass the benefits of having MFA on our sensitive accounts, because someone could access our token AND credentials using only the credentials needed to access our password manager – in other words, using only one authentication factor.
While this may seem overly complicated, it is actually fairly easy to do, and doesn’t mean that we need to use MFA each time we use our password manager. Instead, MFA is typically used to confirm our rights to access the password store when we install the password manager on a new device. After being set up, the password manager will treat the device it is installed on as one of the authentication factors, and can be unlocked by another factor – typically something like our password, our fingerprint, or our facial structure.
It is also important to note that this is one case where it doesn’t really make sense to store a soft token inside our password manager. If we lost access to our password manager and needed to install it somewhere else, we would need to have unlocked the password manager before being able to get the token to unlock it. This is like putting the keys to a box inside the locked box!
For MFA for the password manager, I would recommend one of the following:
- A soft token stored on something like Microsoft or Google Authenticator
- A physical device like the Yubikey (see image), which gives us a physical way to protect our passwords
- Or, less secure but more convenient, configuring our password manager to use One-Time-Passwords (OTP) sent to our phone number as text messages
It is also possible to do more than one of these, for example having a soft token readily available on our phone but having a backup physical device locked in a safe somewhere, just in case we need it.

In summary
If we use all of these recommended steps, our security posture will be much higher than most people’s, making us harder targets for hackers to attack.
Again, I personally recommend 1Password, because I feel that it offers a clear and simple user interface, supports a broad range of platforms, and has sophisticated capabilities, including family sharing and WatchTower, which informs us about compromised websites & passwords, as well as letting us know where we have weak or reused passwords, but there are many others out there that are very robust, including free ones.
As we can see, there is a lot that we can do to protect our digital identity, and therefore many aspects of our online lives. If this all seems a bit overwhelming, I would recommend that you start by using MFA for your more sensitive accounts as this one action will have the most significant impact on protecting you.
What are your thoughts on this topic? I would love to hear from you. Do you have a preferred password manager? Have you had your credentials compromised in the past? Do you already use MFA for some of your accounts? Please get in touch to let me know, but do make sure to not include any sensitive information.
Who am I, and why should you care what I think? Find out more about me here.






No Comments